Pam Shriver - Getting A Grip On Access And Operations
Imagine, if you will, the quiet hum of an incredibly complex system, working diligently behind the scenes to keep our daily lives running smoothly. It's almost like a very intricate dance, with so many parts moving together, and for folks like Pam Shriver, who appreciate precision, knowing how these things are managed can be quite interesting. We often don't think about all the careful steps involved in something as simple as turning on a light switch or getting important information from a large organization, but there's a lot more to it than meets the eye, actually.
When you consider a large operation, perhaps a utility company like Oncor Electric Delivery, there's so much happening that we, the customers, barely ever see. From making sure new construction projects are handled just right to getting power back on after a big storm, it all depends on well-organized processes and clear ways to share information. It's like a finely tuned machine, where every cog and lever has a specific job, and everything needs to be in its proper place for the whole thing to function without a hitch, really.
This whole setup, in a way, relies heavily on how information is handled and who gets to access what. Whether it's about internal procedures, like how employees get their payroll sorted, or making sure sensitive data stays safe from prying eyes, it all comes back to a core idea of careful management. It’s about ensuring that the right people have the right tools and information at the right moment, and that others are kept out, which is quite important, you know.
Table of Contents
- What's the Big Deal with PAM, for Folks Like Pam Shriver?
- How Does the Oncor Electric Delivery System Keep Things Running Smoothly?
- Why Are Manuals Like the Personnel Action Manual So Important for Everyone, Even Pam Shriver?
- Keeping a Watchful Eye: What Does Pam Shriver Need to Know About Security?
- What Exactly is Privileged Access Management, and Why Should Pam Shriver Care?
- Extending PAM Principles: How Can Pam Shriver's Approach Secure the Whole Infrastructure?
- Is Pam Shriver's View on Identity Management Truly Complete?
- Protecting Sensitive Spots: What Accounts Are Most Important to Someone Like Pam Shriver?
What's the Big Deal with PAM, for Folks Like Pam Shriver?
So, you might hear the term "PAM" thrown around in different conversations, and it can actually mean a couple of things, depending on where you are and what you're talking about. For someone who appreciates clarity and order, like perhaps Pam Shriver, understanding these distinctions is quite helpful. Sometimes, "PAM" refers to something very specific, like a Personnel Action Manual, which is basically a guide for how certain procedures are handled within an organization. It's a set of instructions, you know, for employees to follow when they need to make changes or requests related to their work life. This kind of PAM is about keeping things organized and making sure everyone follows the same rules, which is, in a way, pretty important for fairness and consistency.
Then, there's another "PAM," which is a really big topic in the world of keeping information safe and sound, and that's Privileged Access Management. This kind of PAM is all about security, making sure that only the right people can get into the most sensitive parts of a computer system or network. It's like having a very special set of keys for the most important rooms in a building, and you need to know exactly who has those keys and what they're doing with them. This is, arguably, a critical part of protecting an organization's most valuable digital assets, and it’s something that any careful individual, like Pam Shriver, would certainly want to understand.
Both types of PAM, in their own ways, are about establishing order and control. One helps manage people and their actions within a company, making sure processes are followed. The other helps manage who has access to the most powerful parts of a digital system, preventing unauthorized entry and potential problems. They both contribute to a sense of security and reliability, which is, you know, something everyone values. It's really about making sure things are done the right way, every time, and that there are clear guidelines for how to operate, whether you are dealing with paper forms or intricate computer networks, which is quite fascinating, honestly.
How Does the Oncor Electric Delivery System Keep Things Running Smoothly?
Imagine the constant work involved in keeping electricity flowing to homes and businesses; it's a massive undertaking, really. At a place like Oncor Electric Delivery, they have systems in place that are just, well, amazing in their ability to manage all the moving pieces. For example, their automated construction information system, or ACIS, is a central hub where a lot of the planning and tracking for new projects happens. When you need to get into this system, it's pretty straightforward: you just enter your login ID and password, much like you would for any secure online service. It’s their way of making sure that only authorized personnel can access and update critical construction details, which is quite sensible, actually.
And it's not just about construction. If you're a customer, you can easily check the status of your Oncor Electric Delivery account. This means you can keep tabs on your service, which is a nice convenience. They also provide updates on power restoration, which is, you know, incredibly important when there's an outage. They even make sure this information is available in Spanish, which is a thoughtful touch, making it accessible to a wider group of people. The employees at Oncor are, in fact, always working tirelessly to get any remaining customers back online as quickly and safely as possible, showing a clear dedication to their service, you know, which is something you can really appreciate.
This whole setup, you see, highlights the importance of clear access points and readily available information. Whether it’s for internal staff managing complex projects or for customers needing updates during an emergency, having reliable systems in place is absolutely key. It’s about creating a seamless experience, where people can get what they need without unnecessary hurdles, and where the operations behind the scenes are managed with a great deal of care and efficiency. This sort of smooth operation is something that, like Pam Shriver's precision on the court, requires a lot of practice and a good system, basically.
Why Are Manuals Like the Personnel Action Manual So Important for Everyone, Even Pam Shriver?
Think about any large organization, and you'll quickly realize that having clear rules and procedures is just, well, essential for things to run smoothly. This is where manuals, like the Personnel Action Manual (PAM) and the Payroll Procedures Manual (PPM), come into play. These aren't just dusty old books; they're actually living documents that guide how employees manage important aspects of their work life, from payroll details to personnel changes. For someone who values order and fairness, like perhaps Pam Shriver, the existence of such detailed guides is a real comfort, as it means everyone is playing by the same set of rules, more or less.
These manuals, you see, aren't just for show. They undergo revisions, meaning they're updated regularly to reflect any changes in policy or law. This ensures that the information is always current and relevant, which is pretty important. There's even a specific form and process for requesting revisions to these manuals, and this is typically handled by specific employees, like those in a Service Center Operations (SCO) department. This structured approach means that changes are carefully considered and implemented, preventing confusion and making sure everything stays accurate, which is, in a way, a very good thing.
The core idea behind these manuals is about achieving compliance. In simple terms, it means making sure that the organization follows all the necessary rules, regulations, and internal policies. A well-maintained PAM, for instance, is absolutely critical for this. It helps ensure that every personnel action, from hiring to promotions to departures, is handled consistently and legally. Without such a guide, things could easily become messy, leading to errors or even legal issues. So, in essence, these manuals are the backbone of fair and consistent operations, providing a clear roadmap for everyone involved, and that's something even someone with a very busy schedule, like Pam Shriver, would surely appreciate, you know.
Keeping a Watchful Eye: What Does Pam Shriver Need to Know About Security?
When we talk about keeping things safe in the digital world, it's a bit like having a very alert security guard constantly on duty. The ability to monitor and detect suspicious events in any environment, especially a computer network, is incredibly important. It's not enough to just have locks on the doors; you also need to know if someone is trying to pick those locks or if something unusual is happening inside. For someone who understands the importance of strategy and defense, like Pam Shriver, this concept of constant vigilance would resonate quite strongly, I imagine. It's about being proactive rather than just reactive, which is a key difference, actually.
However, just having the tools to watch isn't enough on its own. You also need a very clear focus on what truly presents the biggest risk. It's like having a security camera, but if you don't know what you're looking for, or if you're watching the wrong things, it won't be very effective. You need to understand which areas are most sensitive, which accounts hold the most power, and what kind of activities would signal a real problem. Without this clear focus, you could be overwhelmed by a lot of noise and miss the truly important signals, which is, you know, a common pitfall.
This is where a thoughtful approach to security comes in. It's about more than just technology; it's about strategy and knowing where to direct your attention. It's about identifying the most valuable assets and the most likely threats, and then setting up your monitoring to specifically look for those things. This kind of targeted surveillance is what makes a security system truly effective, helping to catch problems before they become big issues. It’s a bit like a seasoned professional, perhaps like Pam Shriver, knowing exactly where to place her attention to anticipate the next move, making all the difference, basically.
What Exactly is Privileged Access Management, and Why Should Pam Shriver Care?
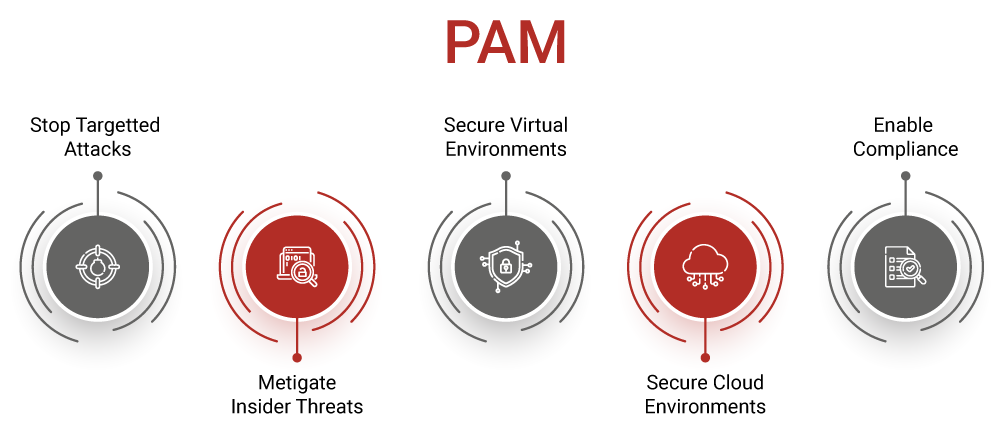
So, let's talk more about Privileged Access Management, often called PAM for short, in the context of digital security. This isn't just some technical jargon; it's actually a very crucial security strategy for controlling and monitoring access to the most sensitive accounts within a computer system. Think of these "privileged accounts" as the master keys to the entire digital kingdom. They can do almost anything, from changing system settings to accessing confidential information, which is, you know, a lot of power. For anyone concerned with keeping things safe and secure, like Pam Shriver might be with her own valuable information, understanding PAM is incredibly important.
This guide, in a way, helps explore just how vital PAM is. It's about making sure that only the right people, at the right time, for the right reasons, can use these powerful accounts. It's not just about stopping outsiders; it's also about carefully managing what insiders can do. This includes things like making sure people don't share their master passwords, or that their actions are recorded so there's a clear trail if something goes wrong. It's a fundamental layer of defense, really, that protects an organization from both accidental mistakes and malicious attacks, which is quite a big deal.
PAM is a specialized type of identity management. While identity management generally deals with who you are in a system, PAM goes a step further by focusing specifically on those accounts that have extraordinary powers. It's a branch of cybersecurity that puts a very strong emphasis on the control, monitoring, and protection of these highly sensitive accounts. It’s about putting very strict limits and oversight on who can do what with the most powerful tools, basically. This kind of careful, focused approach is what helps prevent major data breaches and keeps critical systems running smoothly and securely, offering a great deal of peace of mind, even for someone as busy as Pam Shriver, honestly.
Extending PAM Principles: How Can Pam Shriver's Approach Secure the Whole Infrastructure?
Now, once you understand the core ideas behind Privileged Access Management, you can actually start to apply those same principles to a much wider area. It's not just about protecting a few super-user accounts; it's about extending that careful, controlled approach to manage access across the entire infrastructure. This means thinking about every part of the digital environment, from servers and databases to network devices and cloud services, and making sure that access to all of them is managed with the same level of scrutiny. For someone who thinks strategically, like Pam Shriver, seeing how a good idea can be applied more broadly is pretty interesting, I think.
The goal here is to implement what we call "robust infrastructure access management." This means creating a very strong and reliable system for controlling who can get into what, no matter where it is in the network. It's about building layers of protection and making sure that every entry point is secure. This might involve things like requiring multiple forms of verification before someone can access a critical server, or automatically changing passwords for privileged accounts on a regular basis. It's about taking the best practices from PAM and applying them everywhere, essentially, to create a much safer overall environment.
This extended application of PAM principles helps to reduce the overall risk of a security incident. By carefully managing every privileged connection and action across the entire digital landscape, you close off many potential avenues for attack. It makes it much harder for unauthorized individuals to move around within a system, even if they manage to get a foothold somewhere. It’s a comprehensive way of thinking about security, ensuring that the strongest protections are in place not just for a few key areas, but for the whole operation. This kind of thoroughness is something that, you know, really sets apart a well-protected system, and it's a level of care that anyone, including Pam Shriver, would likely appreciate in a security setup.
Is Pam Shriver's View on Identity Management Truly Complete?
When we talk about identity management in the world of computers and networks, it's basically about figuring out who is who and what they're allowed to do. But for someone with a very precise way of looking at things, perhaps like Pam Shriver, it’s important to ask if that picture is truly complete. Privileged Access Management, or PAM, is actually a very specific kind of identity management. It doesn't just look at everyone; it zeroes in on those accounts

Pam - cháu gái tập đoàn may mặc là em bé Việt đầu tiên có loạt ảnh đạt

Privileged Access Management (PAM) in the Cloud
A Closer Look at Identity and Access Management (IAM) and Privileged